Cyber Attack
Different wireless or wireless/wired networked systems, both military and civil infrastructures, require different frequencies to operate effectively.
They may use standard protocols and routing rules or ad-hoc infrastructures and the information exchanged can be clear or encrypted.
In all the cases, they can be modelled as a network of computing systems.
For a number of years, military operations have used electro-magnetic attacks to disrupt enemy radars on the battlefield.
Today the access and manipulation of the EMS and/or the data and information carried by EMS let us foresee many additional capabilities involving Electronic Warfare (EW) and Cyber Warfare (CW) together.

Figure 1: Traditional EW and CW
Traditionally, Electronic Warfare (EW) and Cyber Warfare (CW) were considered as independent disciplines.
However, because communication systems have moved to commodity hardware and radar and navigation systems began to depend on wireless networked operations, the boundaries between the two fields have begun blur.
Convergence between EW and CW mitigates the differences creating a new parallel for common ops. They together can provide effects that deny or degrade spectrum allowing for the control and exploitation of the network.
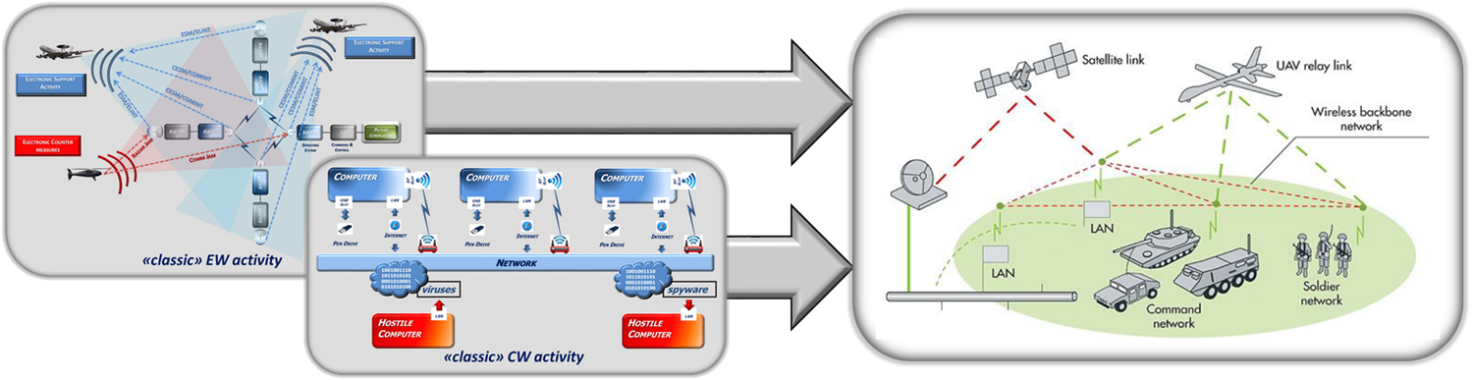
Figure 2: convergence between EW and CW
EW and CW can cooperate to accomplish Cyber missions in the Electro Magnetic Environment (EME).
They can be used in conjunction and thus may be viewed as two sides of the same coin, which is often indicated as Cyber EW or Cyber Electromagnetic Activity (CEMA).
“The synchronisation and coordination of cyber and electromagnetic activities, delivering operational advantage thereby enabling freedom of movement, and effects, while simultaneously, denying and degrading adversaries’ use of the electromagnetic environment and cyberspace” *
*CEMA Capability Integration Group (CIG)
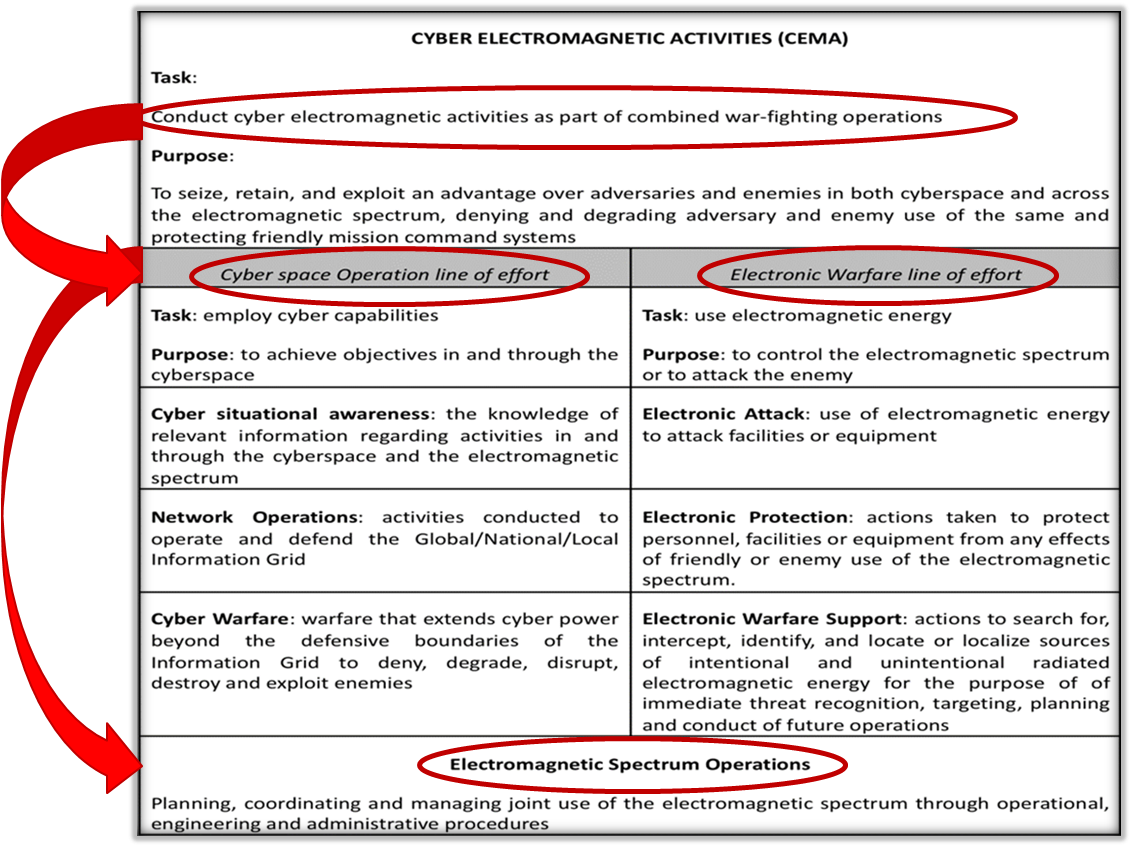
Figure 3: CEMA Overview
Information Operation layers
We can define three different layers of information operations with increasing complexity:
• PHYSICAL LAYER, where the information overlaps with the physical world.
Targets for attack in this layer: physical emissions
• INFRASTRUCTURAL LAYER, that has the task to encode, route, encrypt and deliver the information to the correct endpoint: the “consumer”.
Targets for attack in this layer: frames, packets, sessions, signalling and control.
• COGNITIVE LAYER, where human decision-making takes place.
Targets for attack in this layer: perceptions, emotions, awareness and understanding
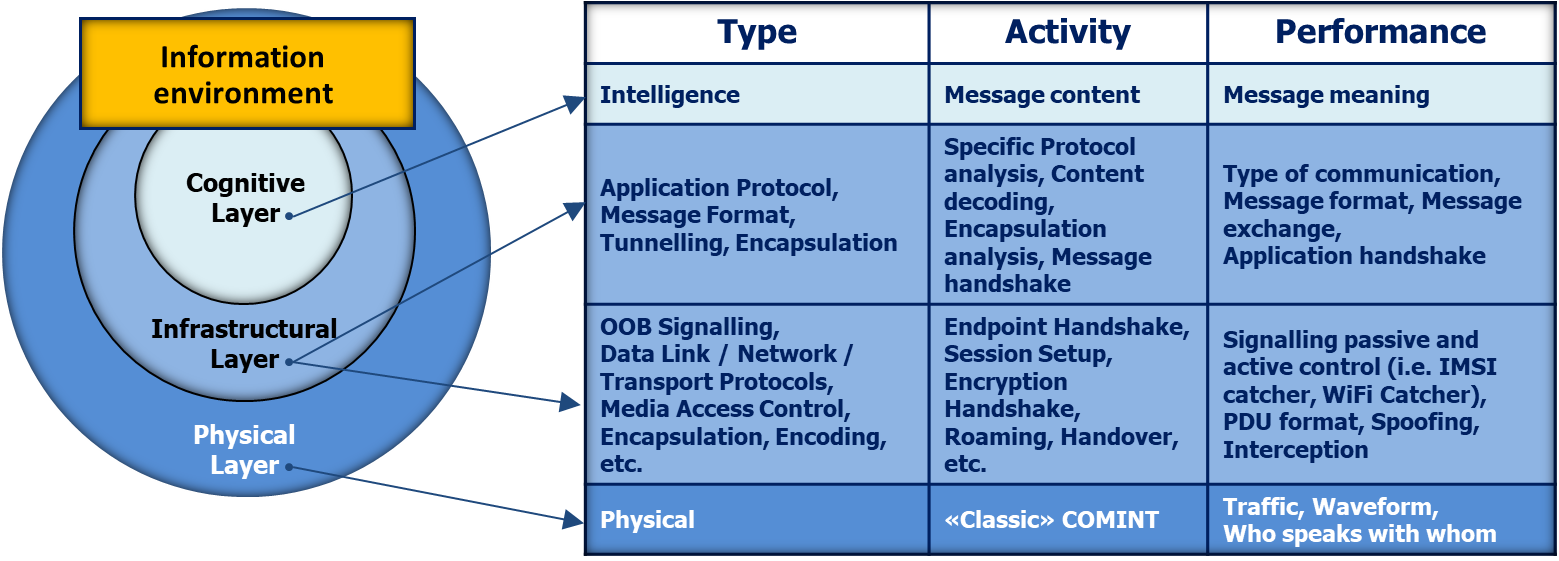
Figure 4: Communication layers
Any of these layers can be separately attacked. Of course by increasing the complexity of the layer also the complexity of the attack will increase, but also the covertness of the attack will decrease accordingly. This means that if the attack is made to the physical or low protocol layer it will be easily discovered while it will be very difficult or even impossible to discover an attack to the content of the information.
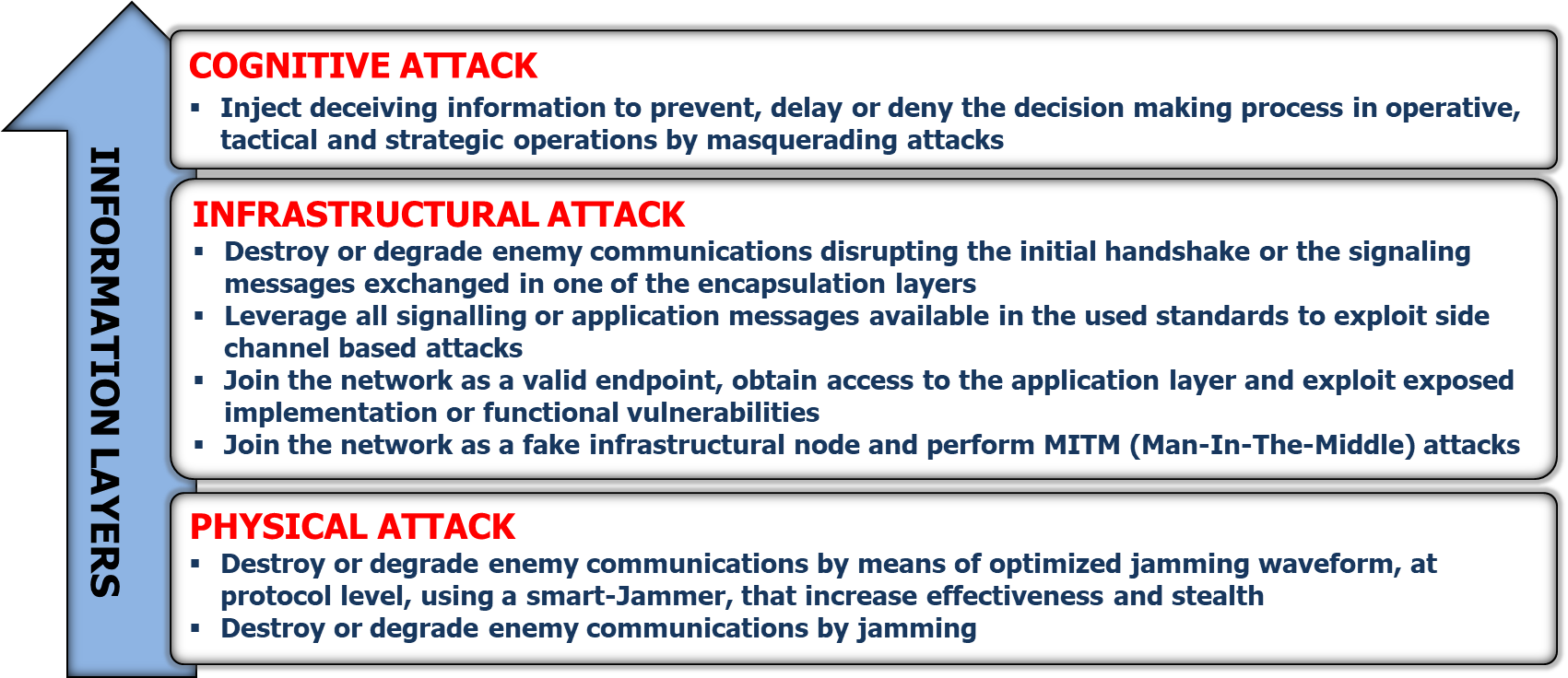
Figure 5: Classes of Cyber-attacks to a communication system
The payload can consist in Viruses, Computer Worms ,Trojan Horses and Spyware and can be activated inside the first networked computer (“n-click”) and then bounced back to the other servers and computers/computing systems via the wired and wireless networks.
The nodes of networked systems physically reside in one of the warfare domains (air, land, sea, space), but the ability to achieve the mission objectives cannot be separated from the ability to control and to have freedom of action in cyberspace that, in this sense, is transversal to all other domains.
The design, development and execution of a Cyber EM operation needs:
• Detailed knowledge of the target:
◦ key to address when attacking the application layer
◦ multidiscipline intelligence
• Being trusted part of the network:
◦ key to inject, manipulate or modify the information transmitted inside a wireless network
• Crack the COMSEC and TRANSEC network protections:
◦ different levels of complexity in term of robustness and resilience
◦ success NOT ensured a-priori
◦ expertise, tools, methodology of REVERSE ENGINEERING
• Deal with preparation and verification issues:
◦ Digital laboratory
◦ Numerical simulation, digital RIG, HW in the loop
• Deal with validation issues:
◦ open air test range facility
As seen in Figure 6 a Cyber Attack Mission can be summarized in five subsequent phases:
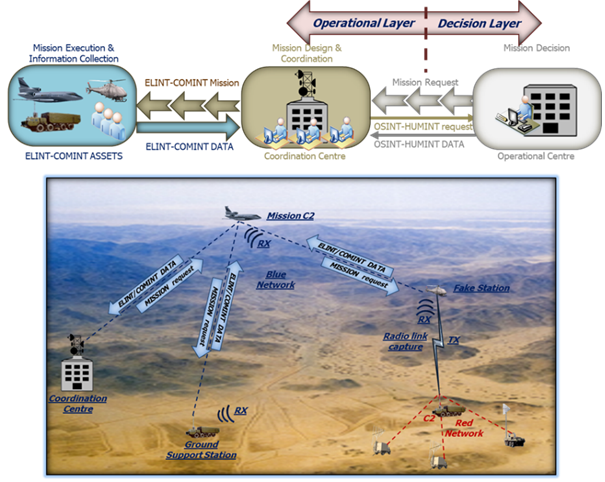
Figure 6: Cyber-attack mission summary
• Phase 1 (Data collection):
The first phase is an Intelligence mission concentrated to the capture of data relevant to the analysis of the opponent communication network.
The Coordination Centre deploys the assets (platforms and sensors) according to the operational conditions.
A picture compilation is synthesized in real time locally in each sensor/platform, whose contributions are available in the distributed data space and correlated/fused in the Coordination Centre (OBSERVE).
Partial view of the same picture are distributed to the platforms, according to their role in the operation (ORIENT), so that short loop adjustments of the mission can be decided at platform level and contribute to the refinement of the picture (DECIDE & ACT).
The mission is also supported by one or more unmanned platforms that must go very close to the opponent network acting as fake stations to enter in the network and acquiring all the information needed.
Figure 7: Data Collection
• Phase 2 (Data Analysis):
A CETL (Cyber Evaluation Test Laboratory) composed by DMISS (Data Mining Intelligence and Surveillance) and DIGILAB allows to perform the following activities:
◦ Reverse Engineering: process of analyzing the target communication device to identify its components and their interrelationships and to investigate how it works to understand the weak points of the architecture (hardware and software) and produce a set of data (device vulnerability)
that feeds (among others) the DATA analysis activity.
◦ DATA Analysis: process of analyzing the opponent communication networks in order to state what is the protocols they are using to communicate (Protocols Structure Analysis), locate the nodes of the intercepted network (Geolocation Analysis) and reconstruct the network topology (Hierarchical Analysis). These activities are all preliminary to the Vulnerability Analysis and Assessments that are necessary to perform an attack at the opponents’ infrastructures.
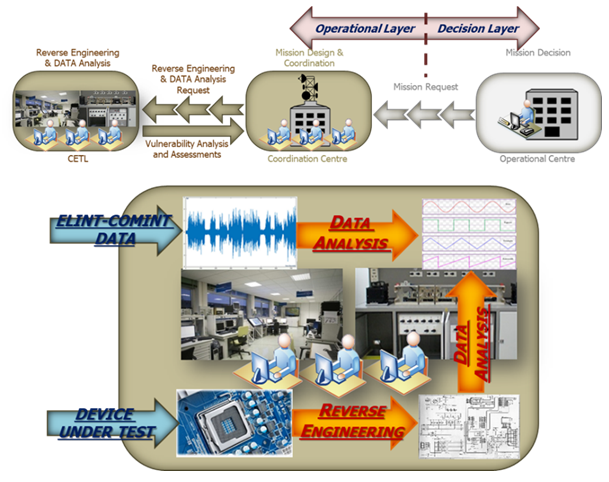
Figure 8: Reverse Engineering and Data Analysis
• Phase 3 (Payload preparation):
This is another activity performed by CETL.
It consists of the process for testing advanced cyber technologies in laboratory environment with realistic and quick replica of interconnected networks to test securely new cyber payloads.
CETL is capable of rapid re-configuration, of emulating a large diversity of networks, and has the flexibility to handle multiple activities simultaneously at different classification levels.
CETL provides a broad range of uses, such as advanced cyber research and development of new capabilities, analysis of effectiveness, cyber training and exercises and is exploited in three subsequent phases for complete environment realistic simulation and cyber applications validation:
◦ a numerical simulation network
◦ A digital RIG
◦ A complete RIG with real HW in the loop
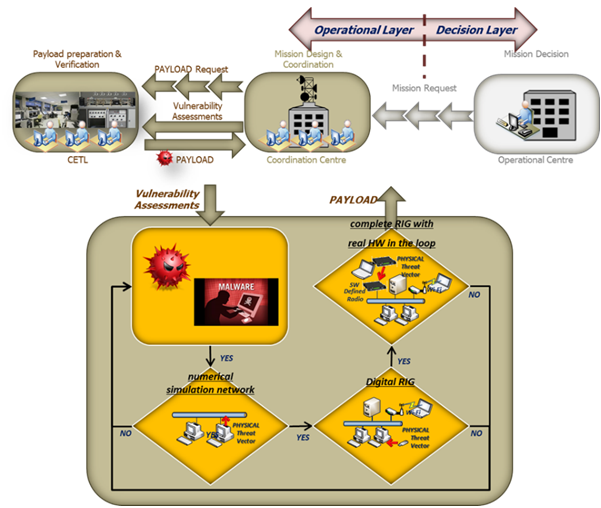
Figure 9: Payload preparation
• Phase 4 (Payload test):
CECR (Cyber Electronic Combat Range) is an open-air test range dedicated to military exercises and tests for Cyber EW systems.
CECR is used for Cyber Payload Test in order to achieve its Validation.
The test range provides a mixed environment of real, emulated and simulated elements in order to grant the operators a place where to test different capabilities of cyber electronic warfare systems that include:
◦ Detection of network attacks (passive protection);
◦ Techniques of network protection (active protection), for example, reconfiguration of network devices;
◦ Techniques of attack to adversary network’s nodes;
Even if the test range is open-air, elements of the network may be linked to wired network (emulated or simulated): essentially, they operate as gateways between wireless and wired portion of a network. Attacks through these elements may have an impact on systems connected to the network.
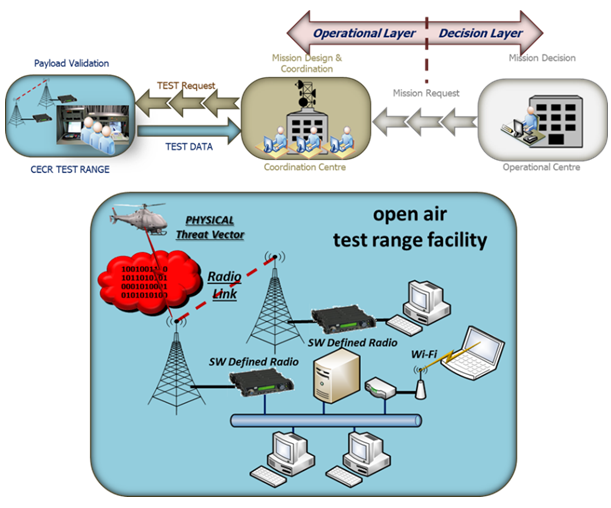
Figure 10: Payload test
• Phase 5 (Cyber-Attack execution):
In this phase the cyber-attack mission is executed, the threat vector is an unmanned platform (or a swarm of unmanned platforms).
A special mission aircraft acting as “mission C2” and flying at very high altitude and at a safe distance from the playground in order to have a good visibility of the Electromagnetic Order of Battle (EOB) can manage the attack mission.
The attack platforms fly at a very low altitude (in order to be as less detectable as possible) towards the playground.
The mission C2 can download updated mission data packages in the attack platforms (real time information) and can act as early warning giving to the mission platforms the indication of incoming threats (according to the EOB and to the platform course).
In addition, the unmanned platforms are boosted by AI that can compensate the residual inaccuracy in mission programming with its flexibility to dynamically changing behavior during the mission course.
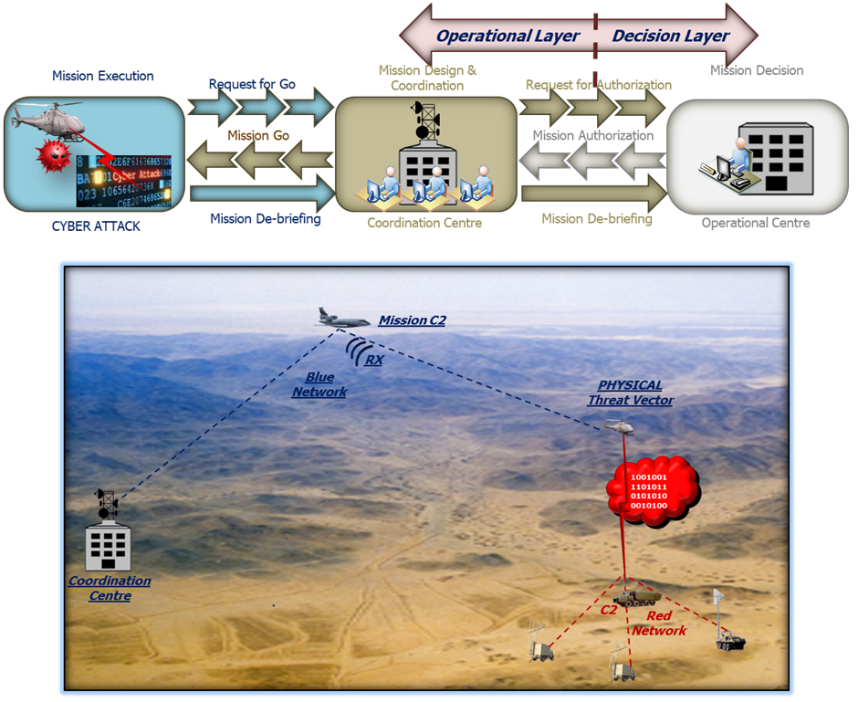
Figure 11: Cyber Attack







