Cyber Protection / Cyber Resilience
Cyber resiliency is the ability to anticipate, withstand, recover from, and adapt to adverse conditions, stresses, attacks, or compromises on systems that use or are enabled by cyber resources.
Conceptually, Cyber Security is shaped by a series of measures focused on reacting to threats that your IT systems are facing.
Whilst implementing basic cyber security best practice could prevent the great majority of attacks, even with your cyber defences up, hackers will find holes when the landscape changes.
Cyber Resiliency, conversely, means, not only to react/protect, but also to be able to anticipate, respond and recover from a cyber-attack, keep operating through adversity (very important) and eventually get back on track and be more capable of withstanding future disruption.
One of the reasons for the emergence of “cyber resilience” lies with the realistic view that for all the defences an organisation might have in place, there is still a probability that they’ll suffer some kind of attack.
Therefore, Cyber Security and Cyber Resilience are different but symbiotic.
Some companies do still treat them as separate but inter-related solutions, often establishing cyber security and resilience policy frameworks and strategies. However, there is more value when cyber security forms an element of overall cyber resilience.
Cyber resiliency concepts are related to the problem domain and the solution set for cyber resiliency.
The concepts are represented in cyber resiliency risk models and by cyber resiliency constructs.
The constructs are the basic elements of the conceptual framework and include goals, objectives, techniques, implementation approaches, and design principles.
The framework provides a way to understand the cyber resiliency problem and solution domain:
- Goals and Objectives identify the “what” of cyber resiliency—that is, what properties and behaviours are integral to cyber resilient systems.
- Techniques, implementation approaches, and design principles characterize ways of achieving or improving resilience in the face of threats to systems and system components (i.e., the “how” of cyber resiliency).
- Solutions typically implement mechanisms which apply one or more cyber resiliency techniques or approaches or which are intended to achieve one or more cyber resiliency objectives.
Cyber resiliency constructs address adversarial and non-adversarial threats from cyber and non-cyber sources. The concern for cyber resiliency focuses on aspects of trustworthiness—in particular, security and resilience—and risk from the perspective of mission assurance against determined adversaries (e.g., the advanced persistent threat).
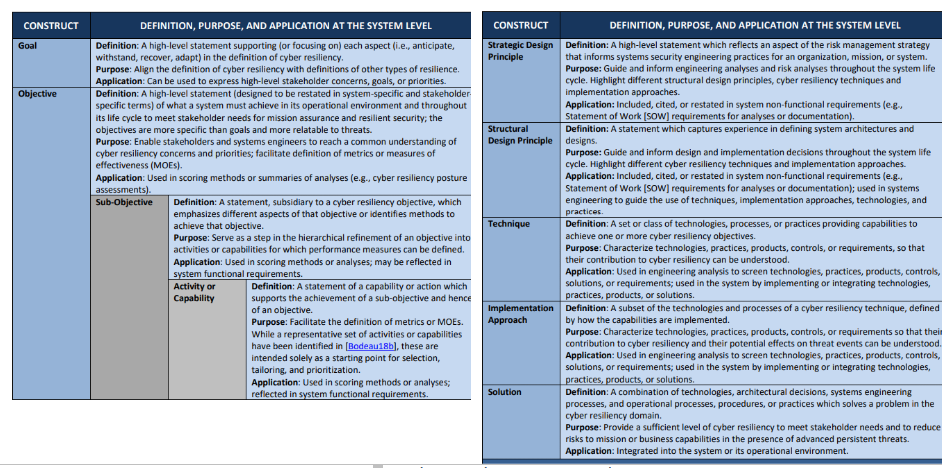
Figure 1: Cyber Resilience construct
Four are the cyber resiliency goals, common to many resilience definitions:
- Anticipate: Maintain a state of informed preparedness for adversity.
- Withstand: Continue essential mission or business functions despite adversity.
- Recover: Restore mission or business functions during and after adversity.
- Adapt: Modify mission or business functions and/or supporting capabilities to predicted changes in the technical, operational, or threat environments.
The term adversity specifically includes stealthy, persistent, sophisticated, and well-resourced adversaries (i.e., the APT) who may have compromised system components and established a foothold within an organization’s systems.
Cyber resiliency objectives are more specific statements of what a system must achieve in its operational environment and throughout its life cycle.
Objectives can be tailored to reflect the organization’s missions and business functions or operational concept for the system-of-interest. Tailoring objectives can also help stakeholders determine which objectives apply and the priority to assign to each objective.
According to the customization process, two examples of bespoke goals follow:
Scenario Example 1:
- Prevent or avoid: preclude the successful execution of an attack or the realization of adverse conditions.
- Prepare: maintain a set of realistic courses of action that address predicted or anticipated adversity.
- Continue: maximize the duration and viability of essential mission or business functions during adversity.
- Constrain: limit damage23 from adversity.
Scenario Example 2:
-
- Reconstitute: restore as much mission or business functionality as possible after adversity.
- Understand: maintain useful representations of mission and business dependencies and the status of resources with respect to possible adversity.
- Transform: modify mission or business functions and supporting processes to handle adversity and address environmental changes more effectively.
- Re-Architect: modify architectures to handle adversity and address environmental changes more effectively.
Cyber resiliency technique is a set or class of practices and technologies intended to achieve one or more goals or objectives by providing capabilities.
Fourteen techniques are part of the cyber resiliency engineering framework (Figure 2).

Figure 2: Cyber Techniques Table
Each technique is characterized by both the capabilities it provides and the intended consequences of using the technologies or the processes it includes.
The cyber resiliency techniques reflect an understanding of the threats as well as the technologies, processes, and concepts related to improving cyber resiliency to address the threats.
The cyber resiliency techniques will be selectively applied to the architecture or design of organizational mission or business functions and their supporting system resources, and are expected to change over time as threats evolve, advances are made based on research, security practices evolve, and new ideas emerge.








