Counter UAS/UAV
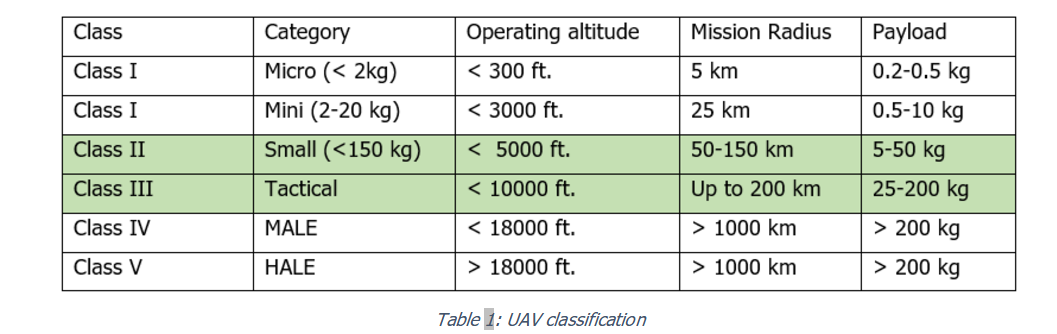
Table 1 gives the commonly accepted classification of UAV, as a function of weight, altitude and payload (source: U.S. Army Roadmap for UAV 2010-2035).
Differently from the case of mini-micro drones (case treated in Counter-Drone Lemma), based on COTS and rapidly available technology, class II and III UAS require a higher level of engineering and are still currently operated by military and symmetrical forces.
Counter-UAS are applied both in military field (protection of high value installation) and in civil field (protection of sensitive targets against terrorism).
Installation in military mission theatre will include the hard-kill effectors to shot down the UAS; more caution must be kept when the UAS is near to civil or sensible targets.
In those cases, the shooting down of the UAS may be not suitable and non-kinetic technique must be used.
Therefore, a Counter UAS System (CUAS) demands detection with multiple sensors operating in different domains, reliable identification capability, real time data fusion, and smart jamming techniques.
• Main characteristics:
◦ Open, flexible, modular and scalable architecture based on a plug-and-play component approach that allows deployment of specific configurations adapted to the threat scenarios.
◦ Detection, recognition, classification, identification and assessment balanced across the adopted sensors and timely reported to the central C2 to reduce operational work force load and bottlenecks.
◦ Command and control: Mission planning, Data fusion, System monitoring, TEWA (Threat Evaluation and Weapon Assignment), Decision support, Result assessment and reporting, Subsystem’s dynamic deployment and integration.
◦ Security and Interoperability: lowest possible security classification level and interoperability with other C2 systems (e.g. air defence systems) at higher security classification level.
◦ Deployment: fixed and deployed “pop-up” applications.
• System capabilities:
◦ Detect, classify, track, identify and counter UASs (single and/or multi-UAVs) in defence scenarios using multiple technologies; the ability of the proposed solution from detection to counter UASs also in civil scenarios is considered a significant plus;
◦ Deliver and update real-time operational picture and alerts;
◦ Integrate into multilayer C2 system with cross-security-domain approach.
Two main operational modes can be identified:
▪ Soft
▪ Hard (integrating Soft Kill capabilities and supporting functions)
◦ Provide a range of selective mitigation alternatives with the ability to evaluate mission success probabilities and resulting drawback;
◦ Require limited logistic support for deployment and maintenance;
◦ Require minimum operator effort for decision making;
◦ Provide dynamic scalability of sensors and effectors;
◦ Facilitate the incorporation of counter UASs in security and defence systems for fixed and deployed asset;
◦ Operate in a wide range of climate (e.g. arctic, subtropical) and weather (e.g. rain, fog, snow) conditions.
• Specific challenges:
◦ Detection & Tracking: low speed, low altitude, very small RF, thermal and acoustic signatures, high manoeuvrability.
◦ Countering: threats are getting resilient to First Generation C-UAS systems that rely on “traditional” detection and neutralization, flying in swarm, possibly boosted by autonomous guidance, using “per-opportunity” data-link and communication means (i.e. 5G). Hard kill not always applicable due to scenario constraints.
◦ Application: from individual soldier, vehicle and command post to larger critical infrastructures, including urban areas.
◦ Design: inherent modularity, scalability and interoperability.
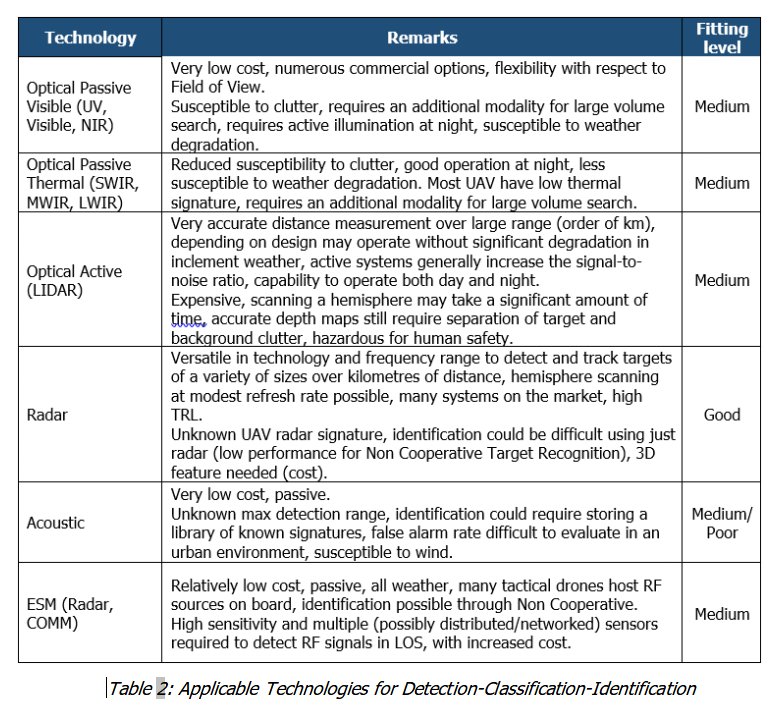
• Detection-Classification-Identification
It is the collection of different kinds of information by one or several sensors.
It includes also a process of discrimination, whose goal is to separate real targets from highly cluttered, noisy or friendly background data.
When this step is performed solely by a human, considerable care must be taken to understand how nuisance alarms affect the overall performance of the system.
Sensors’ inter-designation, cooperation/fusion, correlation will be useful to perform a good spatial survey and effective detection. Geo-location (typically through radar) and finger printing (through EW) could be a distinctive performance for correct discrimination and classification purposes.
Software and AI-based modules at C2 level would be of utmost importance.
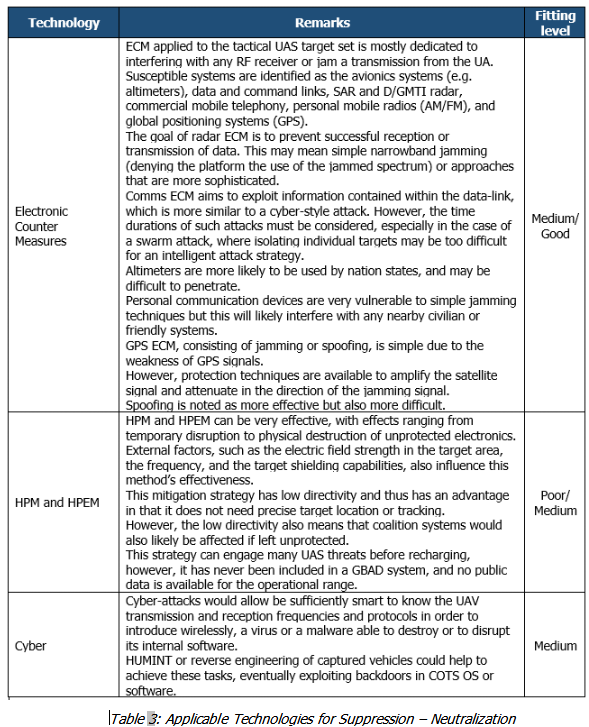
• Suppression – Neutralization
Once a target is classified and identified in the previous step and when a possible threat is confirmed, additional actions must be taken to deny UAV mission success, including the target neutralization through soft measures, in support to kinetic kill (which remains the ultimate goal of an Air Defence system).
Some rules must be followed:
◦ Some types of weapon systems may not be appropriate because of safety constraints and risk of collateral damages near to civilian infrastructures
◦ The interception range, or the range of influence of an effector, must be greater than the potential stand-off range of the UAV, in the event that the UAV is carrying a threat payload (or the UAV is the payload itself)
The effector may dictate requirements on one or more sensors, for example in terms of target designation, tracking and high data refresh rate. This is also true in the opposite direction, where the most effective sensors may restrict the type of mitigation method. In essence, the two must complement one another so that the system is most effective.
Five types of effectors could be considered to deny tactical UAV missions:
◦ Missiles
◦ Guns
◦ Power Laser systems
◦ Electronic Counter Measures, including Cyber attack
◦ High Power Microwave/High Power Electromagnetic Weapons
A Counter UAS System (C-UAS) demands detection with multiple sensors operating in different domains, reliable identification capability, real time data fusion, and smart jamming techniques.
A local command and control station (CUAS C2) integrates and connects all the active and passive sensors and the effectors.
This C2 station implements automatic procedures and rules in order to focus human operations on action, resources coordination and cooperation.
As none of the sensors nor the shooters previously described can be considered as a “silver bullet”, the core of the solution is the C2.
The SW logics of the C2 play an essential role, because the most important requirement of such applications is the reaction time and no human is able to manage the amount of data/information and the complexity of the technology deployed in the short time (few seconds) needed to alarm and counter act.
As an example, Figure 1 shows the typical range of effectiveness of the main sensors and shooters of a Counter-UAS solution, which gives the idea of the reaction time needed to guarantee a fit-for-purpose probability of success.
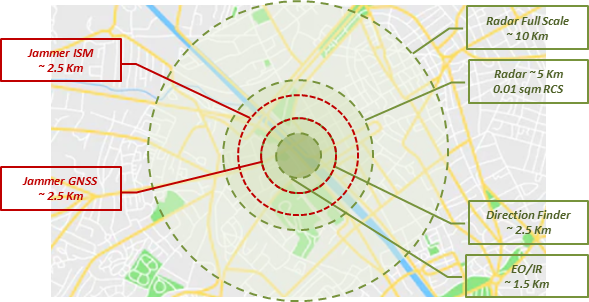
Figure 1: Example of Local Area protection Layers
As the battle-space becomes more complex and the requirement for faster decisions and reactions increases, there is a growing need for automated expert systems for functions as sensor data interpretation and “Automatic Target Recognition-Classification-Tracking”, based on anomalous behaviour detection systems, trained on “standard” behaviour data.
Other AI-based systems, known as “Decision Support Systems”, have broader applications in the C2 environment because they assist the human in the organization of knowledge.
The emphasis is on the support to decision-making, as this involves formulation of alternatives, analysis of their impacts, and interpretation and selection of appropriate options for implementation.
All these support systems included in the C-UAS C2, that aid humans in mission planning, information management, situation assessment, and decision-making, are based on a sort of automation of the OODA (Observe, Orient, Decide, and Act) loop.
Modern views of the OODA cycle have introduced the capability to improve the decision based on the experience (LEARN), which could be apparently obvious but requires methods, information storage and sharing and related procedures of verification-validation when automation is applied to operational context.
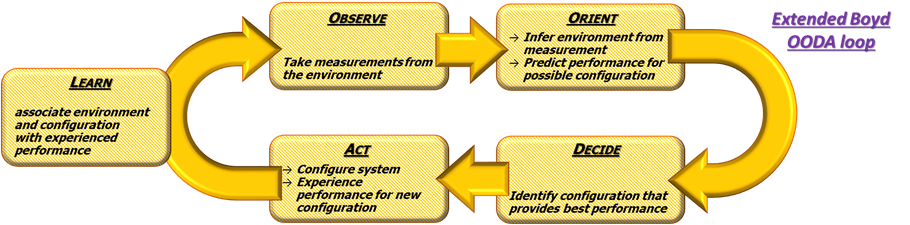
Figure 2: Extended OODA loop
Figure 2 summarizes the four steps of the original cycle, as Col. Boyd described them plus the one that transforms the OODA loop in Extended OODA loop.
The Counter UAS System (C-UAS) can also be a local cell of a wider area protection system whose purpose is to protect sensitive sites/critical infrastructures sparse over a large area.
This will be achieved by a system of systems net-centric architecture integrating different layers of protection (Figure 3).
A number of C-UAS Cells (U-SHORAD, Ultra-SHOrt-Range Air Defence) are integrated with V-SHORAD (Very-SHOrt-Range Air Defence) assets to form a number of local area protection cells (lower operational layer) that are federated in an upper operational layer (Common Command Post, C-POST) acting also as SHORAD (SHOrt-Range Air Defence).
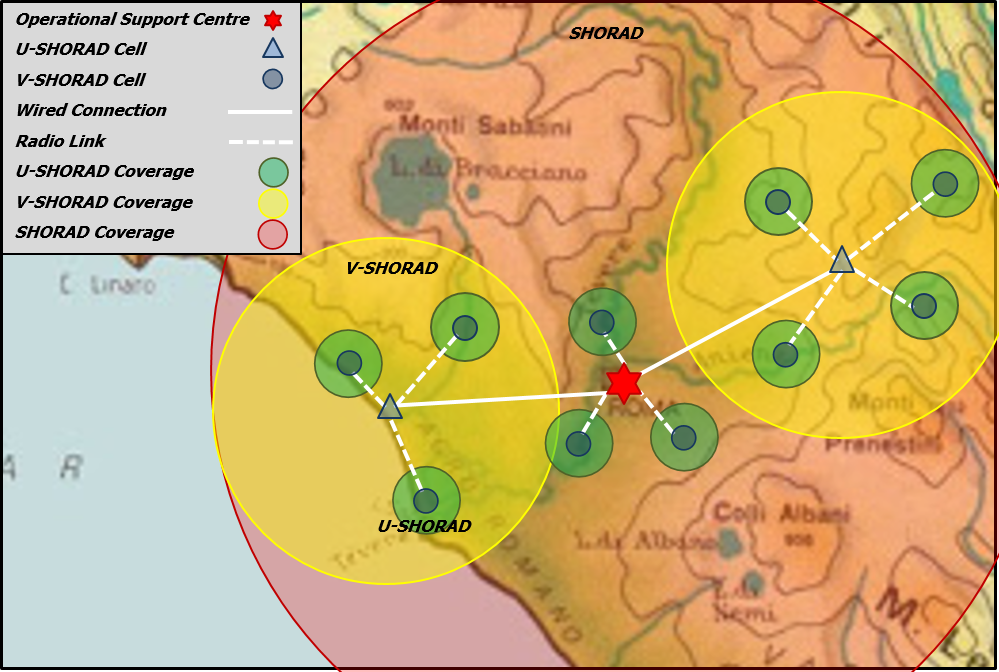
Figure 3: Net-Centric Architecture
A central concentrated intelligence (powered by AI and ML CONCENTRATED INTELLIGENCE) resides in the upper operational layer acting as System C4.
The assets in the lower operational level cooperate with each other under the control of the higher level and are equipped with AI and ML (DISTRIBUTED INTELLIGENCE) which act as subsystem C2.
Any of the assets (whatever the level) is composed by a very varied panel of sensors and/or built-in or external effectors (soft kill and hard kill), correlated and associated through dedicated software, driven by an internal C2 software.
The networked and integrated architecture allows operating as a single system, each sensor of a local cell, in addition to managing the area entrusted to it, can act as an early alarm for the sensors of other cells, functioning as a pre-alarm and giving a real increase in response time.
The Integrated Area protection System of Systems acts as a brick in the territory Air Defence and is integrated at operational level with other components of the IADS.








