Net-centric EW
Definitions
Networks are force multipliers and NCEW takes the principles of NCW, typically the reliance on sharing ISR data, and applies this to electronic warfare.
One could argue that NCEW falls within the Electronic Support element of the EW triumvirate alongside Electronic Attack and Electronic Protection.
The US Department of Defence Dictionary of Military Terms defines Electronic Attack as “actions taken to prevent or reduce an enemy’s effective use of the electromagnetic spectrum, such as jamming and electromagnetic deception.”
This is achieved through the “employment of weapons that use either electromagnetic or directed energy as their primary destructive mechanism.”
Electronic Protection involves “actions taken to protect personnel, facilities and equipment from the effects of friendly or enemy employment” of electronic attack.
Finally, electronic support comprises “actions taken by, or under direct control, of an operational commander to search for, intercept, identify and locate sources of intentional and unintentional electromagnetic energy for the purposes of immediate threat recognition.” Although distinct strands of electronic warfare, these pillars are intertwined.
For example, electronic attack and electronic protection cannot be performed without adequate electronic support.
Tactics
NCEW exploits a simple Aristotelian principle, chiefly that the sum is greater than its parts. Consider a standard large-scale military deployment supporting simultaneous operations in the land, sea and air domains.
Participating aircraft, ships and some ground vehicles will possess EW systems.
These platforms will be outfitted with a plethora of electronic support subsystems.
These could include Radar Warning Receivers (RWRs) that fulfil a tactical function.
They alert a crew that their platform has been illuminated by a radar and may provide details on the radar’s location, type and characteristics, known collectively as its parameters. Some platforms may also possess Electronic Support Measures (ESMs).
These will perform a similar function to the RWRs but provide more detailed parameters and may also be capable of collecting Electronic Intelligence (ELINT) on multiple radar threats simultaneously.
ESMs collect ELINT at tactical, and possibly operational and strategic levels depending on their sophistication.
Meanwhile, dedicated Signals Intelligence (SIGINT) platforms, be those SIGINT satellites, ships, aircraft or ground systems, will collect Communications Intelligence (COMINT) on hostile communications systems and networks, along with ELINT.
This is done principally at the operational and/or strategic level.
The trove of SIGINT collected by these platforms is either analysed as it is collected, or after a mission.
This raw data is mined for intelligence relevant to the ongoing operation.
For example, COMINT may be exploited to reveal the position of red land forces based on their communications emissions.
Likewise, an uptick in communications traffic determined by the COMINT trawl could indicate that red forces are planning manoeuvres.
Operational-level ELINT data collected by these SIGINT platforms could include the disposition of hostile ground-based air surveillance or fire control radars supporting the red force’s integrated air defence system.
This could enable blue air forces to plan their ingress and egress routes to avoid heavily defended parts of red force territory.
Once the raw data is sorted for relevant COMINT/ELINT it is disseminated to the commanders and personnel who need this information to support their missions.
This can be a ponderous process that slows the speed at which relevant SIGINT is available to those who need it.
Meanwhile, SIGINT collected at the tactical level may not necessarily be shared more widely. This may mean that tactically/operationally relevant SIGINT, which could assist other missions, is at best neglected and at worst lost.
Networking
The network forms the basis of an information infrastructure that allows for centralized interpretation, operational control and the distribution of situation awareness to all platforms. Put simply, information is the fuel that makes the decision process run, enabling armed forces to effectively manoeuvre and coordinate actions that target and engage hostile forces.
- NCEW attempts to improve the way SIGINT is shared at operational and tactical levels.
This is key to improving the electromagnetic situational awareness of the blue force.
In a nutshell, blue force platforms will not only collect SIGINT to enhance self-protection but will share this across the force in near real time using Line-of-Sight (LOS) and Beyond LOS (BLOS) communications links.
The sharing of relevant EW information across a force is not a new concept.NATO’s Link-11 TDL uses LOS and BLOS communications links on frequencies of two megahertz/MHz to 29.9MHz, and 225MHz to 399.975MHz to support maritime operations. Link-11 carries written track and tactical information formatted in so-called M-Series messages across networks of up to 61 subscribers that include ships, aircraft or shore installations.
Over this decade, Link-11 will be replaced by NATO’s Link-22 that will use similar wavebands, but will facilitate communications at higher data rates, 12.6 kilobits-per-second/kbps compared to the 1.1kbps of Link-11. Link-22 will also support up to 125 subscribers.
Like Link-11/22, NATO’s Link-16 TDL, which uses frequencies of 960MHz to 1.215 gigahertz/GHz and mainly supports air operations, can share written tactical information, including electronic warfare data, between aircraft, ships and ground installations like airbases and ground-based air defence systems, using J-Series formatted messages.NATO is now taking the NCEW capability enshrined in these TDLs a step further via its Cooperative ESM Operations (CESMO) effort.CESMO (Figure 1) emerged from NATO’s Standardisation Agreement-4658 (STANAG-4658) ratified in 2015.
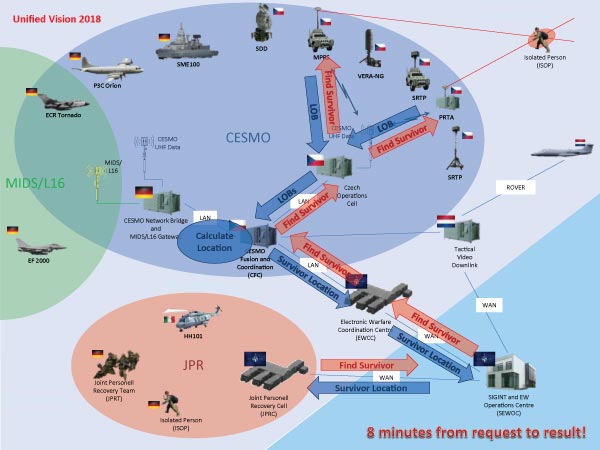
Figure 1-CESMO (NATO) – This diagram illustrates how the CESMO architecture will network air assets to one another to enable the position of hostile radars to be determined and for this information to be shared rapidly with other aircraft supporting a specific mission or wider air campaign.
This prescribed the architecture for an Internet Protocol (IP) based messaging system employing existing LOS and BLOS air-to-air and ground-to-air/air-to-ground communications networks to handle IP traffic containing parameters of hostile ground-based air surveillance radars and fire control/ground-controlled interception radars in a given area in real time.
This ELINT will be shared with other air platforms and ground installations participating in the air battle.
One crucial aspect of CESMO is that any existing communications network that can handle IP format messages can automatically handle CESMO traffic.
This obviates the need for the alliance to implement new communications networks and update existing communications hardware to host the CESMO network.
CESMO exploits the RWRs and ESMs that equip air platforms to not only collect and share ELINT in real time, but also to provide information on the precise location of these radars. This is achieved through processes known as TDOA (Time Difference of Arrival) and Angle of Arrival (AOA) analysis.
AOA determines the line-of-bearing from one point to another.
This can be illustrated with the example of three aircraft flying near a radar.
One aircraft flies on a north-south bearing towards the radar.
Another one flies from east to west away from it while a third approaches the radar from south to north.
Each of the plane’s RWRs detects the radar transmissions and determines the aircraft’s position relative to the radar: the first aircraft’s RWR determines that the radar is to the south, the second that the radar is to the west and the third that the radar is to the north.
The radar will be located at the position where all these respective RWR bearings cross.
This point is computed by the CESMO software using the ELINT it receives from the aircraft’s RWRs and the aircraft’s position as defined by its satellite navigation system.
Staying with our example, let us suppose that all three aircraft continue to fly their same courses.
The first aircraft is 100 nautical miles/nm (185.2 kilometres/km) from the radar flying north-to-south.
The second aircraft is 150nm (277.8km) from the radar flying east-to-west while the last is 50nm (92.6km) away flying south-to-north.
TOA exploits the fact that radar transmissions move at the speed of light; 161,595 knots-per-second (299,274 kilometres-per-second).
The transmissions will take a different amount of time to reach each aircraft’s RWR.
The radar transmissions will take 0.6 milliseconds to reach the first plane, 0.9 milliseconds to reach the second and 0.1 milliseconds to reach the third.
By calculating the difference in time taken for the radar transmissions to reach each of these aircraft the CESMO software can calculate where the radar is located.
At the start of a specific mission or operation, electronic warfare practitioners will draft a list of participating aircraft and their RWRs and ESMs.
These RWRs and ESMs will be uploaded with details of the hostile radars they may expect to encounter during their missions.
This information could be derived from SIGINT collected at the operational level.
During their mission these ESMs and RWRs will monitor the spectrum for emissions from those radars programmed into their threat libraries.
When the aircraft encounter these radars, their RWRs and ESMs will share this information using IP messaging transmitted using their standard radios.
This information reaches the CESMO Fusion and Coordination (CFC) node.
This uses CESMO software hosted on a laptop, for example, to analyse the radar’s parameters.
Aircraft already supporting missions can use the information to update their flight plans to avoid the radar.
Meanwhile upcoming sorties can be planned to avoid the radar, or kinetic or electronic effects can be brought to bear against the radar to take it out of the fight temporarily or permanently.
As of late 2020, the CESMO architecture has been used by individual NATO members but there is currently no alliance-wide operational CESMO capability.
This would be contingent on NATO preparing its communications networks to support CESMO IP format traffic.
Nonetheless, this could occur within a five-year timeframe, meaning that CESMO could be supporting networked EW operations by the start of next decade. NCEW is not restricted to the air domain.
The US Army is taking an important step regarding its NCEW posture with the introduction of its Electronic Warfare Planning and Management Tool (EWPMT).The EWPMT (Figure 2) is a software-based electronic warfare battle management and command and control system.

Figure 2-EWPMT (US Army) – The EWPMT provides the US Army with an electronic warfare situational awareness and battle management tool. This software exemplifies the NCEW trend and the incorporation of networked electronic warfare in multi-domain operations.The CFC will then accurately compute the position of that radar using AOA and/or TDOA and share this with other aircraft and ground installations on the CESMO network.
It can equip a deployed headquarters and is also available for use on a laptop for mounted and dismounted troops using a software application called Raven Claw.
The EWPMT depicts the position of friendly and hostile emitters, their parameters and electronic attack systems.
This allows EW practitioners to easily visualise the electromagnetic battle and to plan and execute electromagnetic manoeuvre in support of the commander’s intent.
The EWPMT can also depict electromagnetic battle damage, enabling practitioners to adjust their scheme of electromagnetic manoeuvre accordingly.
NCEW will be increasingly important to the fusion of manned and unmanned systems in the battlespace. This approach enables the capability of unmanned systems to conduct EMSO missions in concert with other manned and/or unmanned platforms using a multi-node approach against even more capable integrated systems. An interesting application of the concept of Network-Centric EW is Manned-Unmanned-Teaming (MUT).Mission packages composed by manned and unmanned platforms carrying EW payloads are connected in a networked architecture. Unmanned platforms are included in the Cross-Platform (extended) EW layer of integration being part of the EW network coordinated by manned platform/platforms.
Unmanned platforms powered by Cognitive EW and Artificial Intelligence acquire a near-autonomous capability to perform intelligence missions for multi-domain information superiority and electronic attack missions playing the role of the fighter aircraft wingman (for stand-off electronic attack missions) or deep intruder (for stand-in jamming missions).
This enables coordinated missions of multiple platforms against multiple threats with pre-programmed instructions.
The net-centric mission architecture exploits two integration layers:
- The upper operational layer with a central concentrated intelligence supported by AI.
- The lower operational layer federated inside the upper one connecting manned and unmanned platforms via MUT and also unmanned platforms using AI to provide distributed intelligence.
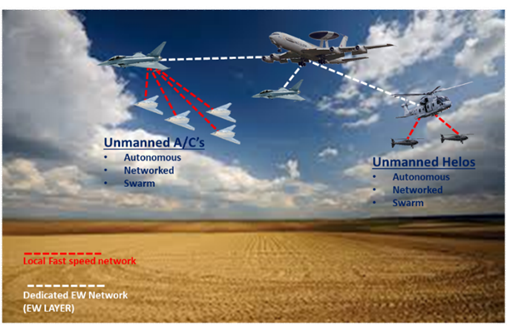
Figure 3: Manned Unmanned Teaming
The presence of AI on-board the unmanned platforms will enable autonomous operations to acquire independently, track and target threats without the presence of a priori precise intelligence.
- Future developments
NCEW will increasingly meld into the prevailing US-driven trend towards Multi-Domain Operations (MDO). This will exploit each mission element or platform as a node operated as part of network that facilitates aggregated, distributed operations.
MDO places a heavy emphasis on the ever-deepening connectivity of military platforms, weapons, bases, subsystems and personnel for the real time sharing of data to provide ever-deepening situational awareness.
In a nutshell, the goal of MDO is to provide all blue force participants with the ability to know exactly what is happening in any part of the battlespace at any given moment using highly robust communications networks while avoiding information deluge through the utilisation of artificial intelligence and machine learning.
The networking of EW assets as shown by initiatives like CESMO and the EWPMT will be absorbed into the wider trends towards MDO seen elsewhere in US and allied forces.
In essence, MCEW provides the EW networking foundation that will become an integral part of multi-domain operations.







