Electronic Attack aka electromagnetic attack
Electronic Attack (EA) missions are performed to degrade either temporarily or permanently enemy electronic sensors (radars and communication receivers) by the transmission of signals designed for that purpose (JAMMING), or to cause enemy systems to acquire and track invalid targets (DECEPTION).
EA can be applied from air, sea, land, and space by manned or unmanned systems, and can target humans, communications, radar, or other assets generally identified as Spectrum Dependent Systems.
In other words, Electronic Attack aims at the Spectrum Dominance in a combat environment.
Electronic Attack, according to the mission performed can be divided in:
-
Offensive Electronic Attack that performs Smart Electromagnetic Neutralization and/or Degradation of the target enemy radars and/or the target communications links to create a safe Electro-magnetic corridor for the protection of one or more friendly platforms (attack package) penetrating the enemy territory.
-
Defensive Electronic Attack that performs Smart Electromagnetic Neutralization and/or Degradation of the use of the Electro Magnetic Spectrum (EMS) to enemy radars for the self-protection of own platform against terminal threats (endgame).
Defensive Electronic Attack is reactive and acting in a multi-spectral domain including the Radio Frequency (RF) and the Electro Optic (EO) domains.
This mission is performed in order to generate Electro-Magnetic signals aimed to induce wrong measurements (angle, distance) or to deny the target detection and tracking to a radar or missile seeker up to the minimum distance possible (burn-through range).
Electronic Attack can be also divided according to the targeted equipment: Communication EA and Radar EA.
Offensive Electronic Attack Mission includes:
-
Escort Task (Escort Jamming, EJ) that is performed by airborne platforms provided with Escort Jamming capability.
The Escort Jammer (EJ) is a Jamming System installed on board an airborne platform (manned or unmanned) or in an external POD.
The EJ platform flies together the defended intruder package.
Escort Jammer is normally exploited for Radar EA. -
Stand-Off Task (Stand-Off Jamming, SOJ) that is performed by an airborne platform flying at a safe distance from enemy assets (high RF transmitted power, low mobility).
Stand-Off can be exploited both for radar EA and for Communication EA. -
Stand-In Task (Stand-In Jamming, SIJ) that is performed flying deeply inside the enemy territory (intruder missions) to target and engage enemy aircraft and air defence systems (low RF transmitted power, high mobility, low Radar cross section, preferably unmanned platforms networked with the protected platforms).
Stand-In can be exploited both for radar EA and for Communication EA.
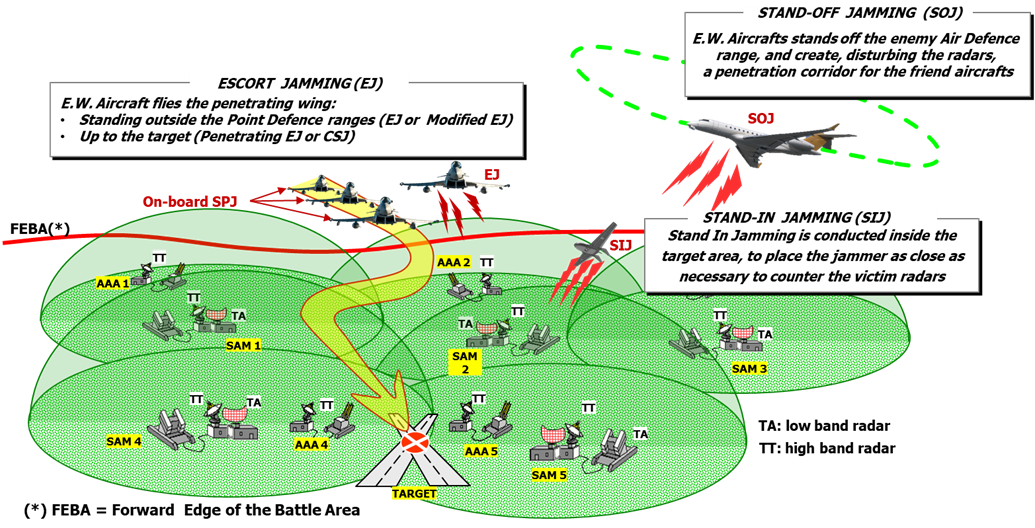
Figure 1: Offensive EA Missions
Defensive Electronic Attack Mission includes Self-protection Task.
-
Self-Protection Task exploits protection of the platform “against lethal attacks by denying enemy use of the electromagnetic spectrum to guide or trigger weapons”.
Self-Protection is a key asset for operations in the battlespace; it assures the survivability and self-protection of the platform, operating in the RF and EO/IR domains.
Self-Protection Task is performed by the Self-Protection Suite (SPS) that is installed in the platform to be defended.
Self-Protection is normally exploited for Radar EA.
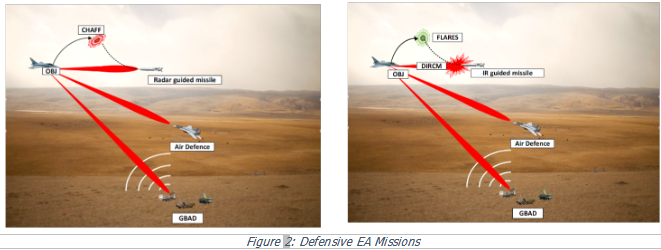
Figure 2: Defensive EA Missions
For a number of years, military operations have used electro-magnetic attacks to disrupt enemy radars or to break enemy communications on the battlefield.
Today the access to the EMS and/or to the data and information carried by EMS has become much wider and wireless networks support data exchange among computers in the battlefield creating a computer communication network based on electromagnetic interconnectivity.
This opens a new entry door for Cyber-attack: new communication jammer must have also the capability to carry Cyber payloads to be delivered to the target computers through the EMS and through the wireless network.
Communication Electronic Attack includes the capability to performing Cyber Warfare: Electronic Warfare and Cyber Warfare work in conjunction and thus may be viewed as two sides of the same coin, which is often indicated as Cyber EW or Cyber Electro Magnetic Activity (CEMA).
CEMA Electronic Attack is defined as Offensive Cyber Operation (OCO) that projects power and a wide range of effects into the adversary’s network through the combination of EW and cyberspace activities.
The key focus of CEMA in OCO is on the cyber and EM capabilities of the adversary, on the detailed collection of all the technical aspects of the employed asset, and on the automated countermeasures and respond procedures.







