Space EW
The value chain of a generic Space System (or System of Systems) is often identified by 4 macro-areas: (1) launch infrastructures, people and tools (2) satellites platforms and payloads (3) ground segment for spacecraft control and radio links (4) services, including remote terminals hardware and software applications.
A large variety of applications and services benefits or directly depend on the use of space and Space Systems. As briefly summarized in Figure 1, exploitation of space and Space Systems can be both military and civil, sometimes overlapping.
The Space value chain permits the delivery of space-based services reliant on satellite technology and includes a wide diversity of stakeholders:
-
Government agencies: fund space technology R&D for their own uses and for dual-uses. Public R&D efforts come from a limited number of countries
-
Space industry: includes a limited number (but rapidly growing) of players who design and manufacture space systems and their launch vehicles
-
Satellite operators: own the satellite systems and market their capacities to service providers
-
Service providers: deliver communications, navigation and geographic information services to the final users
-
Ground segment and terminal supplier: design and deliver a large variety of software and equipment for the management of satellite infrastructure and for the access to services by the users.
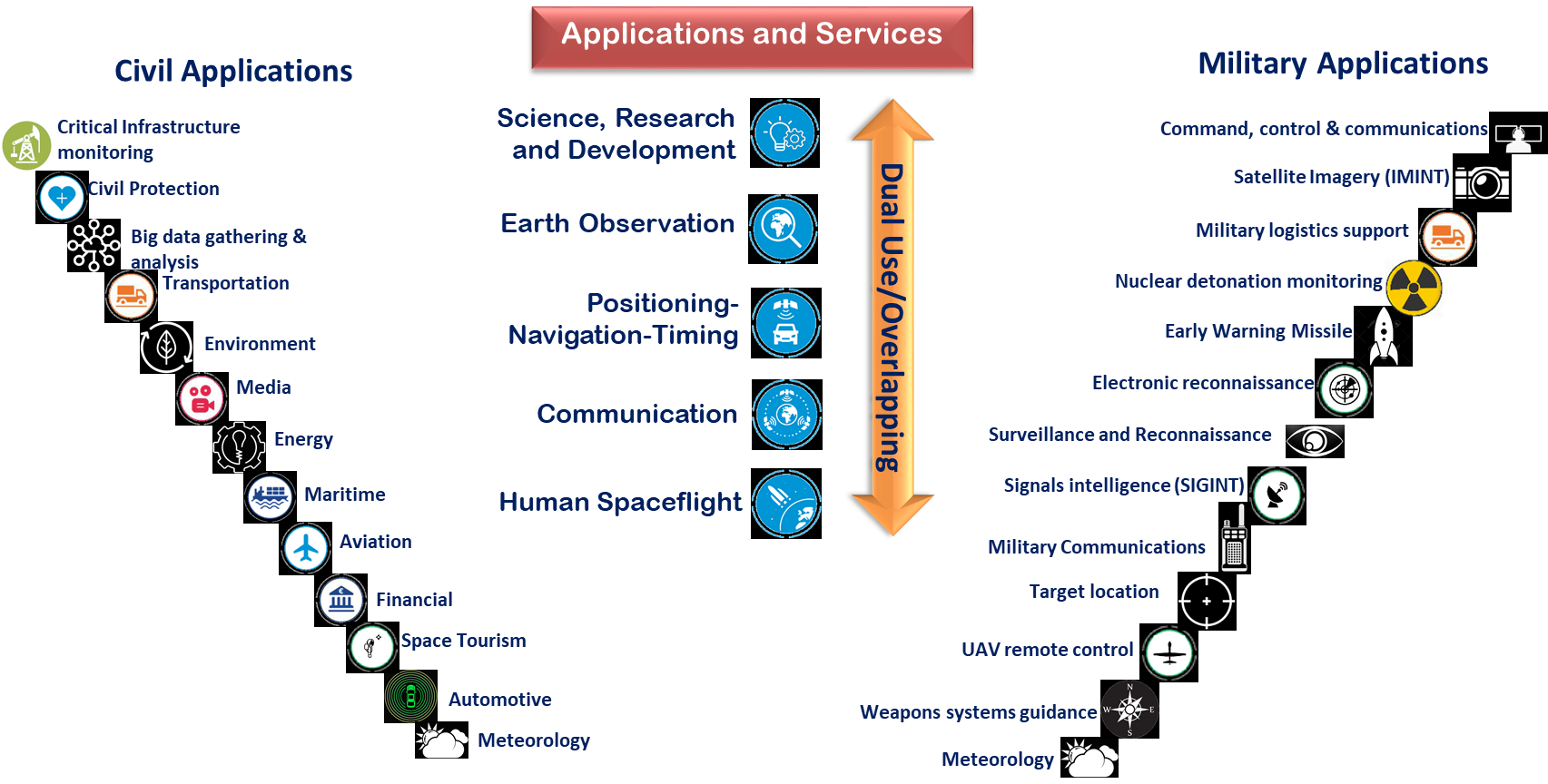
Figure 1: Applications and Services in Space domain
The Space “context” is becoming complicated by the convergence of disparate interests:
-
Space economy is constantly and regularly growing both in strictly connected applications both in related services. The most of the market is covered by civil applications and most of this market is related to ground and added-value services, not to in-orbit assets.
-
The sector is moving from using a few large, complicated and costly satellites to establishing constellations of numerous small and cheap satellites. See cubesat (nanosat), an academia standard which provide a great opportunity to enter easily in the space market: cheap launch (less than 400.000 dollars for LEO) and availability of COTS components (power supply unit, solar panels, antennas, sensors, etc).
-
Always-increasing amounts of data will be produced and related applications, which once were restricted to a limited subset of highly trained users, are becoming more accessible and ubiquitous. Following the entrance of new actors, by the prices are anticipated to decrease in the coming years.
-
Civil and military applications increase synergy: most of the applications are potentially dual use and can grant access to both domains.
Space is essential:
-
to the daily life of the citizens and to the economic prosperity of the countries
-
to the exercise of a strategic autonomy, in terms of:
-
-
capacity for national authorities to decide and transmit its decisions in a sovereign way
-
data gathered through space offered as an exchange good
-
-
for the conduct of military operations around the world.
Given that, an adversary can attack any component of the space chain with the intent to deny the advantages of space reconnaissance:
-
Kinetic Attack, which means physically attacking the satellite or the Ground Segment.
Examples of the first are (1) Direct Ascent ASAT (Anti-Satellite), when a rocket is launched and reaches the altitude of the target satellite, and then either collides with it, or detonates a nuclear warhead: (2) Co-orbital ASAT, when a weapon is positioned in a similar orbit, and then manoeuvre to get close and detonate.
The Ground Segment can be a highly vulnerable target: a large antenna cannot be buried in a bunker, so it is vulnerable to small munitions or even special force attacks.
-
Electromagnetic Attack, which means Offensive Electronic Warfare
Examples are: (1) jamming actions against uplink, downlink, crosslink; (2) jamming actions against the payload, i.e. SAR radar; (3) directed lasers or electromagnetic power transmitters.
-
Cyber Attack, which means hacking activities against one or more components of the Space chain (satellite, ground segment, radio link, or vital services such as Navigation).
Electronic Warfare and Cyber may be the preferred way to attack space capabilities, because they don’t have the same long-term consequences as kinetic attacks on satellites (space debris) and they can’t’ be tracked without a dedicated monitoring system.
As Offensive EW may be one of the preferred way to attack space capabilities, Defensive EW is a good candidate to implement effective protection strategies. Examples of applications are:
-
Avoiding tracking through jamming
A way to avoid tracking is to detect then jam the tracking sensor.
For radar, that means carrying a radar tracking detection payload, also known as a radar warning receiver. Early US film reconnaissance satellites carried such a system, as a part of a “vulnerability payload“. Modern US satellites probably carry the same type of systems. Detection can be also carried out using dedicated signal intelligence satellites. Laser tracking can also be detected in a similar way, whereas optical tracking is completely passive and thus cannot be detected directly.
The next step is then to emit radio waves towards the tracking radar, to interfere with its signal and break the detection, much in the same way a fighter way uses its electronic countermeasures against a ground radar.
-
Detecting the engagement
The terminal guidance of ASAT systems can be either infrared or radar, so countermeasures against both are required. However, a first step before activating countermeasures it to realize that they are needed, by detecting the engagement has taken place. This means the defending side must have a good situational awareness, to detect either that a direct-ascent ASAT has been launched from the ground, or that a co-orbital ASAT made a manouvre to get on a collision course.
Regarding the direct-ascent launch, it can be detected in much the same way a ballistic missile or a surface-to-air missile launch can be. This can be detected by an infrared sensor that can be carried by the satellite. Another way to get notice of a rocket launch is to use sensors on other satellites. This is exactly what dedicated missile-warning satellites, like DSP or SBIRS in the US, do. They keep a constant watch on Earth using infrared sensors, detect any launches and give a rough estimate of their target
-
Jamming
Once the engagement has been detected, the satellite can use electronic systems to jam the terminal guidance of the ASAT weapon. If it is radar-guided, electronic countermeasures similar to those used to jam search and tracking radars might do. If the guidance is infrared however, a different solution needs to be used. Since anti-air missiles often have infrared guidance, directed energy countermeasures have been developed against them. They use an infrared laser precisely aimed at the missile to saturate it or confuse its tracking algorithm. The video below explains how one such system works. Similar systems might be carried by large satellites that have the spare mass and volume to install them.
-
Decoying
The final step in breaking ASAT terminal guidance is to use decoys. It is especially interesting in the case of direct-ascent ASAT: they close the distance with the target so fast that they only have a very limited amount of time to discriminate the real target from the decoys, and if they miss once, they cannot come back for a second attack.
Decoys exist against both infrared and radar seekers. In space, decoys continue on their way. If they are given a small speed at release, they will keep that speed and follow a plausible orbital trajectory. So they cannot be distinguished from a non-manoeuvring satellite based on their motion alone
In any case, resilience and protection of a Space System is essential and has to be included by design. This likely implies:
-
Establishing near-real time Space Situational Awareness (SSA), in LEO and GEO, to detect direct-ascent ASAT launches and manoeuvres by co-orbital ASAT. Ground SSA assets, complemented by the Space Based Infrared Systems (SBIRS) and Geo Synchronous Space Based Situational Awareness (GSSA) satellite constellation, probably already allow an extensive SSA capability. Radar warning receivers carried by the LEO satellites also contribute to the situational awareness.
-
Setting up an integrated and responsive Command and Control architecture, to quickly decide on the course of action after a threat has been detected, and to execute the decisions swiftly. This requires almost constant contact with the satellites. For example, this has been achieved in US through the creation of the National Space Defence Centre.
-
Equipping future satellites with enhanced manoeuvring capabilities and countermeasures to break terminal guidance, to avoid being hit if fired upon. Anti-simulation decoys seem to be a relatively simple and lightweight option, yet like in the ABM (Anti-Ballistic Missile) field they probably pose a serious challenge to most threats.







