Amplitude Modulation in RECM techniques
Amplitude ON-OFF Modulations attempt to force alternately AGC operation for target return in saturation condition and signal suppression (AGC jamming). Successful operation requires AGC jamming to exploit the averaging effect of radar AGC time constant.
Amplitude Modulations are used:
- To support Stealing Techniques (Range/Doppler):
- In the preliminary part of Range and Doppler seduction.
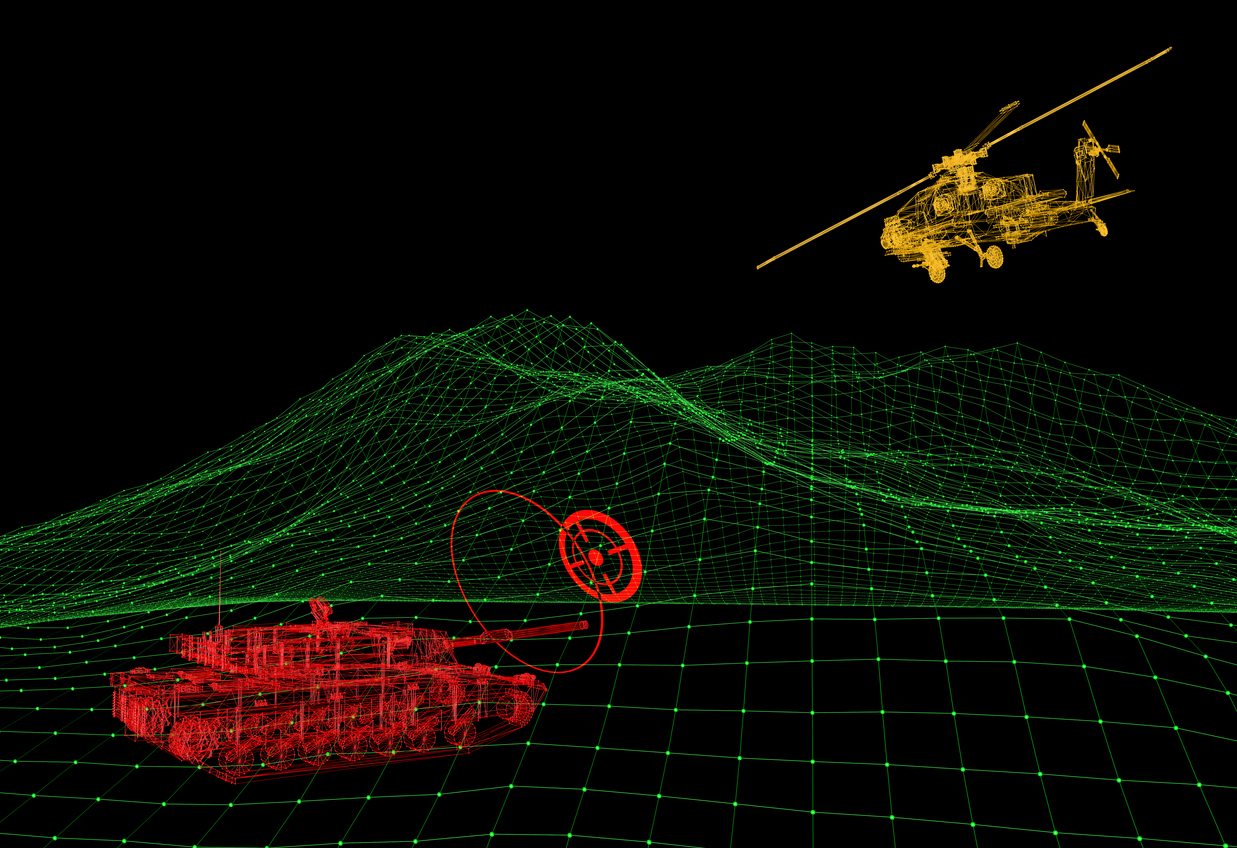
This consists in the “dwell” phase of the gate stealing technique. After the transmission of the first false target, at each subsequent pulse, the intensity of the false echo is increased slightly, to a point far beyond the intensity of the original echo.Then the radar decreases its gain and the contribution of the actual radar return becomes negligible and is no longer distinguishable from background noise (seduction phase or AGC capture). - In the final part of Range and Doppler seduction.
This consists in the “hold” phase of the gate stealing technique. When the radar has been led far enough away in range or frequency, the jammer signal is progressively attenuated and finally is turned off and the radar is left without a target and will need to restart its acquisition process again before it can re-start tracking the actual skin echo.
- In the preliminary part of Range and Doppler seduction.
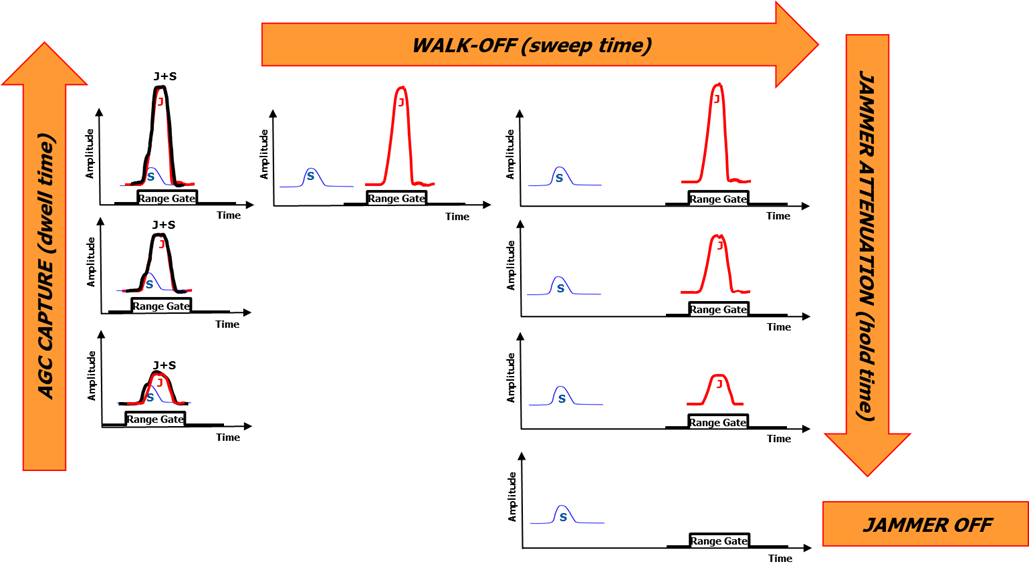
Figure 1: Amplitude Modulation in dwell and hold phases of a gate stealing technique
- To operate an Angle Deception countermeasure, aiming to mislead the tracker from the actual target angle, usually executed after the “hold” phase of the gate stealing technique.
This is achieved by the application of an ON-OFF amplitude modulation jamming (with two periods T on and Toff) that attacks the AGC function of the radar receiver causing the gain-controlled amplifier to cycle between the following two states: -
- During T on the output of the amplifier is at limit level because of the large jammer input.
All signal modulation is lost because of the output limiting. - During Toff the gain of the amplifier is so low (because of the large AGC filter capacitor voltage applied during Ton) that the output signal is too small to be of any use.
- During T on the output of the amplifier is at limit level because of the large jammer input.
We can distinguish two main applications of Amplitude Modulation in Angle Deception, depending on the capability of the jammer to receive the modulation of the radar and then to synchronize its transmission to the received signal:
-
- Inverse Gain:
Inverse Gain Technique is a form of angle deception used against Conical Scan Radars aimed to mislead the tracker from the actual target angle by means of a false-target with synchronized amplitude modulation.
The jammer is able to receive the amplitude modulation from the radar (motion of the detected transmitted beam) and can synchronize its modulation patterns with the motion of the radar beam (Synchronized Inverse Gain to compensate for radar scanning).
- Inverse Gain:
- Swept Amplitude Modulation (SAM):
Swept Amplitude Modulation is applied against radars whose modulation cannot be received by the jammer: they are referred to as Lobe-On-Receive-Only (LORO) or Scan-On-Receive-Only (SORO) systems.
Against these radars, the AM jammer is forced to operate blindly, without synchronization.
The SAM produces an ON-OFF Amplitude Modulation, whose Repetition Interval is frequency modulated around the value of the scan rate of the radar.
This technique assumes the knowledge of the scan rate of the victim radar (Mission Data dependent).
Other applications of Amplitude Modulation are:
- Confusion actions with the purpose of additional effects in relation with radar illumination pattern (transmission in the side-lobes of scanning radars).
- Scintillation according to fluctuation models, to provide realistic features to false echoes.
- Non-coherent Spoofing: generation of a large number of non-coherent false echoes (false detections) in order to overload operator capabilities and automatic radar extractor, obtained by Noise Jamming with superimposed scan synchronous ON/OFF modulations.






![Passive Direction Finding [DF] Techniques – Phase Comparison Passive Direction Finding [DF] Techniques – Phase Comparison](https://www.emsopedia.org/wp-content/uploads/2021/04/iStock-545810334.jpg)