Self-Protection for submarines

Submarines are the least visible of all military assets. While this makes them highly secretive in nature, it also makes them highly valuable. They provide several different functions to navies, many of which affect other military operations.
The submarine’s original role is high intensity operation against surface targets and other submarines. The end of Cold War with its dramatically changed missions, however, requires submarines to have a broader spectrum of capabilities in order to confirm their relevance in the emerging security environment.
Today’s modern submarines are versatile assets in security policy. This is achieved by using state-of-the-art technological solutions in sensors, unmanned underwater vehicles, propulsion and weapons.
Future submarines will become even more flexible platforms by means of applying an even more modular design, which allows the units to be specifically tailored for a wide range of missions across the operational spectrum. Therefore modern submarines are will remain multi-purpose platforms and premier naval units for the foreseeable future.
Today, the submarine’s most important capability is the possibility it offers to operate without directly influencing the scenario:
-
Observation of illegal activities is only possible when the presence of an observer is not known;
-
Radar and COMM ESM can be carried out without known presence of the observer;
-
The delivery of special forces can be carried out uncompromised by detection of the carrier;
-
Invisible force protection is possible if a visible protection is not wanted to avoid escalation of the political situation;
-
Covertness allows the submarine to operate in high threat areas close to the coast, where surface units would be under constant threat from asymmetric weapons;
Designed to be virtually undetectable, submarines are able to patrol the world’s oceans – even in hostile territory. This allows them to:
-
gather intelligence;
-
undertake surveillance and carry out reconnaissance missions;
-
monitor the air, land and sea (both above the surface and below); and
-
act as force multipliers: forcing foreign military to launch several vessels in response to even the threat of a single submarine.
During times of war or regional crisis, submarines are crucial in controlling the seas. Submarines can:
-
-
detect and destroy hostile submarines and surface ships;
-
blockade foreign ports and restrict ocean transport;
-
provide intelligence and underwater protection for surface ships, and are able to detect and lay mines more efficiently than any other navy vessel;
-
provide a means to land special forces in hostile regions; and
-
if fitted with suitable weapons, are able to strike land targets.
-
Compared to other platforms, the submarine is a robust and concealed platform for ESM missions. Collecting radiation data covertly obviously provides inherent benefits: because it is unaware, the opponent displays unaffected behaviour which, in comparison to the self-conscious behaviour typically caused by open surveillance, may furnish information of high tactical relevance.
This capability comes from the submarine’s stealth characteristic: the ability to enter an area to watch, to listen, to collect information without being seen. Therefore, both in times of crisis and in peace keeping operations, a specific role of surveillance and reconnaissance is recognized for such a platform, making them a high value asset needing self-protection capabilities (both soft and hard) against a variety of threats.
Submarines are searched and attacked from air, sea and sub-sea. They hide thanks to silentness, use of environment and of their sensors.
A modern submarine Combat System is composed by:
-
Advanced acoustic sensors (e.g. cylindrical bow arrays, flank arrays on hull side, towed arrays, passive ranging sonar, acoustic intercept sonar)
-
Advanced non-acoustic sensors (e.g. electronic support measures for signal intercept and direction finding, optical and laser range finders; thermal imaging sensors)
-
Automatic rotation, recording and display mast system
-
GPS navigation
-
Modern Communications
-
Advanced multi-processing display
-
High performance data buses for data fusion and information management
-
Advanced Computer Aided C2
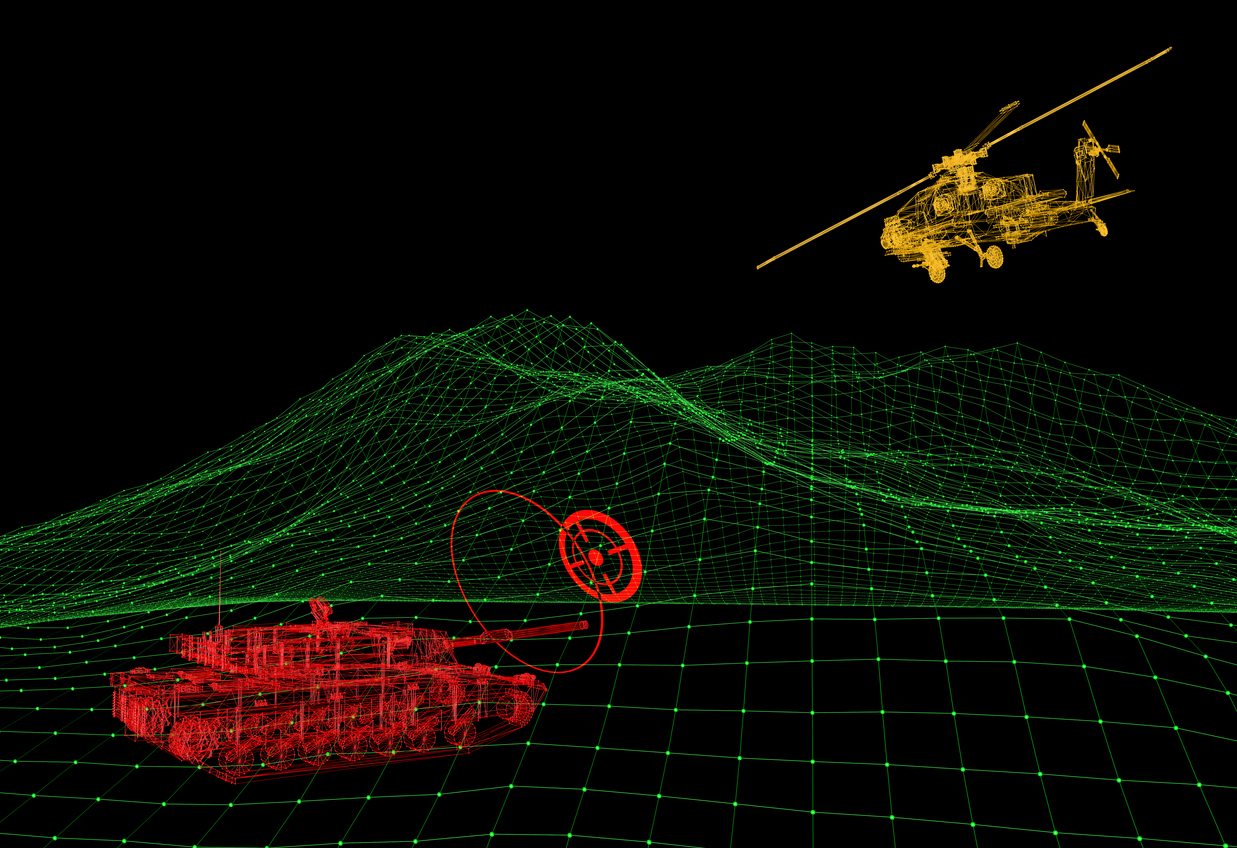
In the field of electromagnetic spectrum observation, all the modern submarines are equipped with Radar ESM, able to perform threat alarm function against Maritime Patrolling Aircrafts and Special Mission Helicopters, employed in Anti-Submarine Warfare (ASW). In the last decade, the rising of asymmetric scenarios posed additional challenges and tasks to submarines, where self-protection and information gathering have become two sides of the same coin.
Advances in technology miniaturization and digitalization, and the synthesis of new materials (i.e. graphene) for radar signature reduction, allow today the interpenetration of threat alarm and ELINT functions in a single multi-functional system with shared resources.
Furthermore, Radar ESM is jointly used with Communication ESM, with COMINT capabilities, enhancing the platform capabilities in terms of:
-
interception, listening, deciphering of mobiles and fixed radios (HF, VHF, UHF, PMR, satellites)
-
intrusion in mobile phone network (2G/3G) however necessitate active network cell emulation thus transmission (IMSI catcher) and a sparse target network
-
interception of vocal, SMS, MMS, data, fax, mails
-
understanding of surveyed communication network architecture
-
possibilities of cyberwarfare through intrusion in mobile networks
-
vocal fingerprinting and tactical or intelligence use of results
-
field of activities mainly ground, few naval (small boats) not air
-
naval traffic following through AIS interception R-ESM/ELINT is mainly useful in symmetrical environment as RF targets are generally not used by asymmetric forces
-
building of coastal naval and air search and defense network
-
interception and recording of LPI radars
-
tactical use through IMOP/UMOP fingerprinting
-
localization of hostile naval assets
-
enrichment of strategic Electronic Order of Battle
-
understanding of hostiles tactical intents through assets (naval, air) move or presence
-
field of activities ground, naval and air R-RWR is mainly useful in symmetrical environment for naval force protection missions and submarine safety or attack missions
-
participate to submarine safety while at periscopic depth
-
enrich and ease targets list and location through sensors fusion
-
enrichment of tactical Electronic Order of Battle






![Passive Direction Finding [DF] Techniques – Phase Comparison Passive Direction Finding [DF] Techniques – Phase Comparison](https://www.emsopedia.org/wp-content/uploads/2021/04/iStock-545810334.jpg)